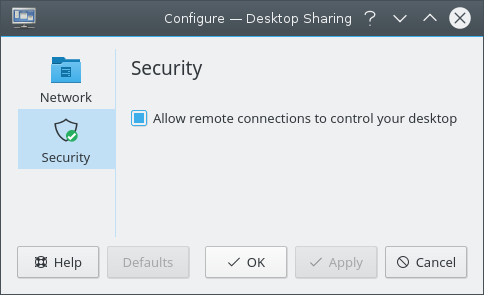
In addition to the main Desktop Sharing interface shown and described above, you can also control Desktop Sharing using the on the Desktop Sharing main window. The Desktop Sharing configuration has two pages, as shown in the screenshot below:
The Network page allows control over the port that Desktop Sharing uses, as shown below.
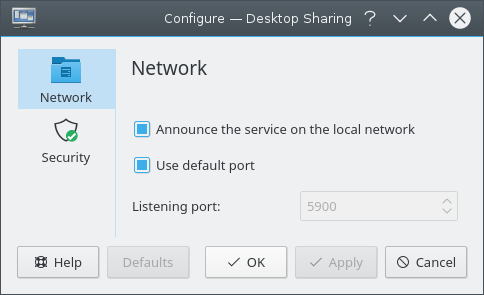
The Announce service on the local network checkbox controls whether Desktop Sharing announces the service over the local network using Service Location Protocol. This is normally a good idea, but only works really well with a Service Location Protocol aware client, such as Remote Desktop Connection.
If you select the Use default port checkbox, then Desktop Sharing will locate a suitable port. If you deselect this checkbox, you can specify a particular port. Specifying a particular port may be useful if you are using port-forwarding on the firewall. Note that if Service Location Protocol is turned on, this will automatically deal with identifying the correct port.
The Security page allows you to configure whether the person connecting to the Desktop Sharing server can control the desktop, or only view.